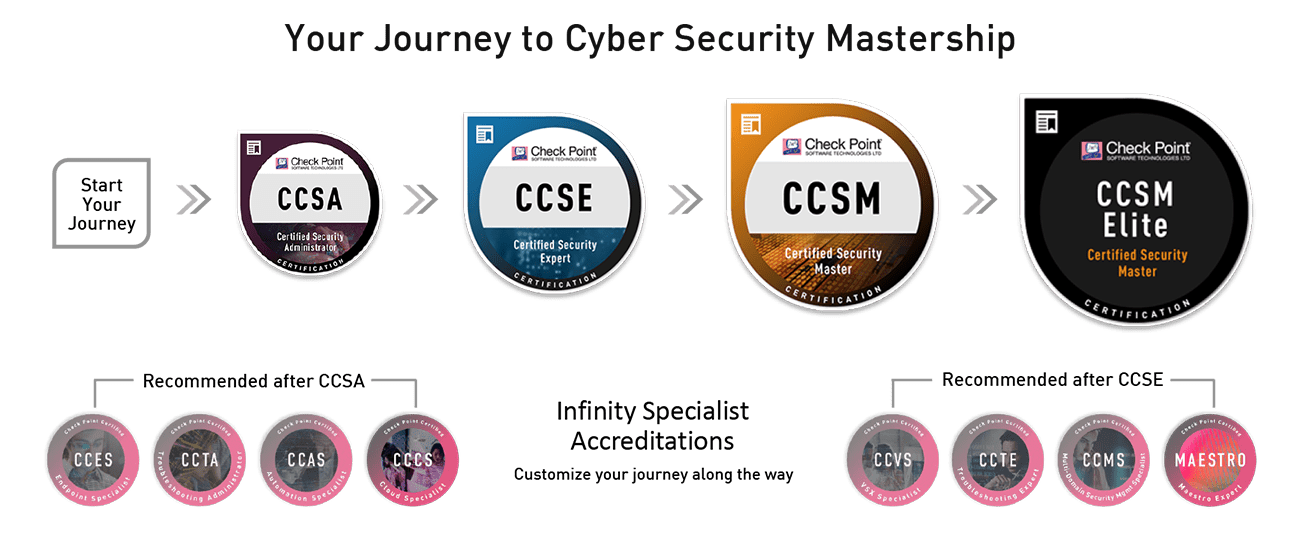
156-215.81 – Check Point Certified Security Administrator (CCSA) R81.10 – Updated November 2021
Authorized Training Center (ATC)
ATC partners are regulated by Check Point to ensure the consistent delivery of high-quality learning experience. This mandates that our delivery utilizes vendor accredited courseware, certified instructors offering real-world experience, digital labs and high-class facilities.
We deliver public and private instructor-led learning services, which can be delivered both face to face in a classroom, virtually online or a combination of the two. Additionally, we provide a range of digital learning solutions including e-learning.
Delivery options include the ability to support standard vendor certification, bespoke and tailored content, ensuring we meet the needs of the learner and organization.
About this Course
-
- Three-day course covers everything you need to start-up, configure and manage daily operations of Check Point Security Gateway and Management Software Blades systems on the GAiA operating system.
Course Goals/Skills
- Know how to perform periodic administrator tasks
• Describe the basic functions of the Gaia operating system
• Recognize SmartConsole features, functions, and tools .
• Describe the Check Point Firewall infrastructure
• Understand how SmartConsole is used by administrators to grant permissions and user access
• Learn how Check Point security solutions and products work and how they protect networks
• Understand licensing and contract requirements for Check Point security products
• Describe the essential elements of a Security Policy
• Understand the Check Point policy layer concept
• Understand how to enable the Application Control and URL Filtering software blades to block access to various applications
• Describe how to configure manual and automatic NAT
• Identify tools designed to monitor data, determine threats and recognize opportunities for performance improvements
• Identify SmartEvent components used to store network activity logs and identify events
• Know how Site-to-Site and Remote Access VPN deployments and communities work
• Explain the basic concepts of ClusterXL technology and its advantages
Intended Audience
- Technical professionals who need to deploy and manage Endpoint Security within their security environment.
Course Format
 |  |
|---|---|
Присъствен (Classroom) Курс в Учебната ни зала или В Офис на Клиент | Онлайн (Online/Virtual) Курс във виртуална зала с инструктор |
Course Language Option:
 |  |
|---|---|
Български (Bulgarian) | Английски (English) |
You can choose the language in which the training will be conducted – Bulgarian or English. All our instructors are fluent in English.
Student Guides:
The training materials are available in electronic format. They can be used online / offline on any device. Lifetime access.
Lab Environment:
Each student has their own lab environment where the exercises are conducted, part of the course. You do not need to install software on a computer or special hardware requirements.
Participants in a face-to-face format in our Training Center have an individual computer during the training.
Course Duration
- 3 working days (09:00 – 17:00 / 9:00 am – 5:00 pm) UTC +2 (contact us for another Time Zone)
or
- 24 learning hours after hours (2 weeks, classes are held 2 times a week in one of the following options):
- Sat. and Sun. 10:00 – 14:00 or 14:00 – 18:00 or 18:00 – 22:00
- Mon. and Wed. 19:00 – 23:00
- Tue. or Thu. 19:00 – 23:00
Payments
You can enroll with your Check Point Learning Credits.
If you are Check Point Partner you can also get free training via the Co-op Program. Check your eligibility and request funds here or For any further questions or additional assistance, please E-Mail: [email protected]
We provide Invoices for Company Sponsored Trainings.
Invoices can be requested up to 7 days after the payment.
Course Schedules
If you dont see a date, contact us.
All classes are confirmed individually after enrollment.
Course Objectives:
• Identify key components and configurations
• Create and confirm administrator users for the domain
• Validate existing licenses for products installed on your network
• Create and modify Check Point Rule Base objects
• Demonstrate how to share a layer between Security Policies
• Analyze network traffic and use traffic visibility tools
• Monitor Management Server States using SmartConsole
• Demonstrate how to run specific SmartEvent reports
• Configure a SmartEvent server to monitor relevant patterns
• Configure and deploy a site-to-site VPN
• Configure and test ClusterXL with a High Availability configuration
• Understand how to use CPView to gather gateway information
• Perform periodic tasks as specified in administrator job descriptions
• Test VPN connection and analyze the tunnel traffic
• Demonstrate how to create custom reports
• Demonstrate how to configure event Alerts in SmartEvent
• Utilize various traffic visibility tools to maintain Check Point logs
Instructors
FAQs
Requirements
- Basic knowledge of networking 6 months to 1 year of experience with Check Point products recommended
Features
- Know how to perform periodic administrator tasks • Describe the basic functions of the Gaia operating system • Recognize SmartConsole features, functions, and tools . • Describe the Check Point Firewall infrastructure • Understand how SmartConsole is used by administrators to grant permissions and user access • Learn how Check Point security solutions and products work and how they protect networks • Understand licensing and contract requirements for Check Point security products • Describe the essential elements of a Security Policy • Understand the Check Point policy layer concept • Understand how to enable the Application Control and URL Filtering software blades to block access to various applications • Describe how to configure manual and automatic NAT • Identify tools designed to monitor data, determine threats and recognize opportunities for performance improvements • Identify SmartEvent components used to store network activity logs and identify events • Know how Site-to-Site and Remote Access VPN deployments and communities work • Explain the basic concepts of ClusterXL technology and its advantages
Target audiences
- Technical professionals who need to deploy and manage Endpoint Security within their security environment.